2017 February Cisco Official New Released 400-251 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
Cisco New Released Exam 400-251 exam questions are now can be download from Lead2pass! All questions and answers are the latest! 100% exam pass guarantee! Get this IT exam certification in a short time!
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-251.html
QUESTION 41
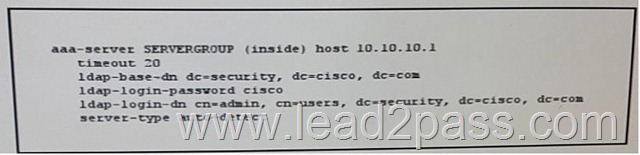
Refer to the exhibit. Which two effect of this configuration are true ? (Choose two)
A. The Cisco ASA first check the user credentials against the AD tree of the security.cisco.com.
B. The Cisco ASA use the cisco directory as the starting point for the user search.
C. The AAA server SERVERGROUP is configured on host 10.10.10.1 with the timeout of 20 seconds.
D. The Cisco ASA uses the security account to log in to the AD directory and search for the user cisco.
E. The Cisco ASA authentication directly with the AD server configured on host 10.10.10.1 with the timeout of 20 second.
F. The admin user is authenticated against the members of the security.cisco.com group.
Answer: CF
QUESTION 42
Which object table contains information about the clients know to the server in Cisco NHRP MIB implementation?
A. NHRP Cache Table
B. NHRP Client Statistics Table
C. NHRP Purge Request Table
D. NHRP Server NHC Table
Answer: D
QUESTION 43
What is the default communication port used by RSA SDI and ASA ?
A. UDP 500
B. UDP 848
C. UDP 4500
D. UDP 5500
Answer: D
QUESTION 44
when a client tries to connect to a WLAN using the MAC filter (RADIUS server), if the client fails the authentication, what is the web policy used tofallback authentication to web authentication ?
A. Authentication
B. Passthrough
C. Conditional Web Redirect
D. Splash Page Web Redirect
E. On MAC Filter Failure
Answer: E
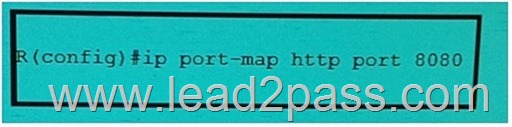
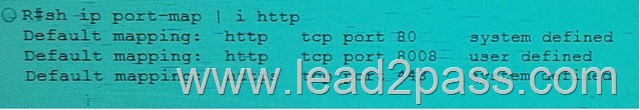
QUESTION 45
Refer the exhibit. Which of the following is the correct output of the above executed command?
Answer: C
QUESTION 46
Which two statement about IPv6 path MTU discovery are true? (Choose two)
A. The discover packets are dropped if there is congestion on the link.
B. the initial path MTU is the same as the MTU of the original node’s link layer interface
C. It can allow fragmentation when the minimum MTU is blow a configured value
D. During the discover process the DF bit is set to 1
E. If the source host receiver an ICMPv6 packet too BIG message from a router it reduces its path MTU
F. IF the destination host receives and ICMPv6 packet too Big message from a router it reduces its path MTU
Answer: BE
QUESTION 47
Which two effects of configuring the tunnel path-mtu-discovery command on a GRE tunnel interface are true? (Choose two)
A. The maximum path MTU across the GRE tunnel is set to 65534 bytes.
B. If a lower MTU link between the IPsec peers is detected , the GRE tunnel MTU are changed.
C. The router adjusts the MTU value it sends to the GRE tunnel interface in the TCP SYN packet.
D. It disables PMTUD discovery for tunnel interfaces.
E. The DF bit are copied to the GRE IP header.
F. The minimum path MTU across the GRE tunnel is set to 1476 bytes.
Answer: BE
QUESTION 48
Which option describes the purpose of the RADIUS VAP-ID attribute?
A. It specifies the ACL ID to be matched against the client
B. It specifies the WLAN ID of the wireless LAN to which the client belongs
C. It sets the minimum bandwidth for the connection
D. It sets the maximum bandwidth for the connection
E. It specifies the priority of the client
F. It identifies the VLAN interface to which the client will be associated
Answer: B
QUESTION 49
You are developing an application to manage the traffic flow of a switch using an OpenDaylight controller.
Knowing you use a Northbound REST API ,which statement is true?
A. Different applications, even in different languages, cannot use the same functions in a REST API at same time.
B. The server retains client state records
C. We must teach our applications about the Southbound protocol(s) used
D. The applications are considered to be the clients, and the controller is considered to be the server
Answer: D
QUESTION 50
Which option describes the purpose of Fog architecture in loT?
A. To provide compute services at the network edge
B. To provide intersensor traffic routing
C. To provide centralized compute resources
D. To provide highly available environmentally hardened network access
Answer: A
QUESTION 51
What are feature that can stop man-in-the-middle attacks? (Choose two)
A. ARP sniffing on specific ports
B. ARP spoofing
C. Dynamic ARP inspection
D. DHCP snooping
E. destination MAC ACLs
Answer: CD
QUESTION 52
Which two statements about CoPP are true? (Choose two)
A. When a deny rule in an access list is used for MQC is matched, classification continues on the next class
B. It allows all traffic to be rate limited and discarded
C. Access lists that are used with MQC policies for CoPP should omit the log and log-input keywords
D. The mls qos command disables hardware acceleration so that CoPP handles all QoS
E. Access lists that use the log keyword can provide information about the device’s CPU usage
F. The policy-map command defines the traffic class
Answer: AC
QUESTION 53
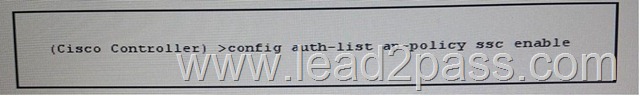
Refer to the exhibit. Which effect of this configuration is true?
A. The WLC accepts self-signed certificates from the RADIUS server to authorize APs.
B. The WLC adds the MAC addresses listed in the ssc ap-policy to its internal authorization list.
C. The WLC adds the ssc access point to the auth-list internal authorization list.
D. The WLC accepts the manufacture-installed certificate from the local access point.
E. The WLC accepts self-signed certificates from devices added to itsa internal authorization list.
Answer: D
QUESTION 54
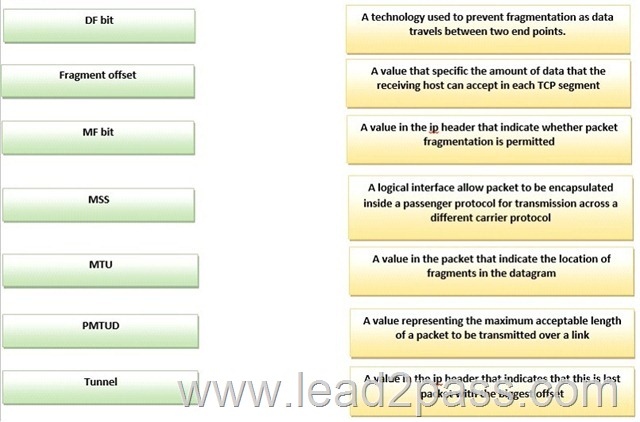
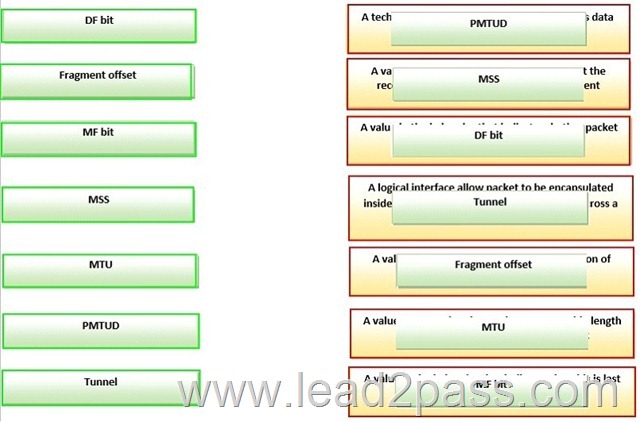
Drag and Drop Question
Drag each ip transmission and Fragmentation term on the left to the matching statement on right
Answer:
QUESTION 55
Which two network protocols can operate on the Application Layer?(Choose two)
A. DNS
B. UDP
C. TCP
D. NetBIOS
E. DCCP
F. SMB
Answer: AF
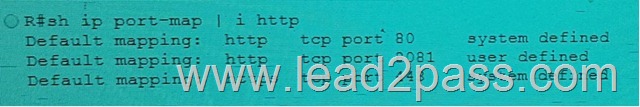
QUESTION 56
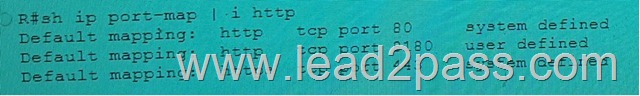
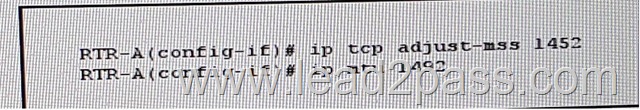
Refer to the exhibit, which effect of this configuration is true?
A. The PMTUD value sets itself to 1452 bytes when the interface MTU is set to 1492 bytes
B. SYN packets carries 1452 bytes in the payload when the Ethernet MTU of the interface is set to 1492 bytes
C. The maximum size of TCP SYN+ACK packets passing the transient host is set to 1452 bytes and the IP MTU of the interface is set to 1492 bytes
D. The MSS to TCP SYN packets is set to 1452 bytes and the IP MTU of the interface is set to 1492 bytes
E. The minimum size of TCP SYN+ACL packets passing the router is set to 1452 bytes and the IP MTU of the interface is set to 1492 bytes
Answer: D
QUESTION 57
Which of the following statement is true about the ARP spoofing attack?
A. Attacker sends the ARP request with the MAC address and IP address of the legitimate resource in the network.
B. Attacker of ends the ARP request with MAC address and IP address of its own.
C. ARP spoofing does not facilitate man in-the-middle attack for the attacker.
D. Attacker sends the ARP request with its own MAC address and IP address of legitimate resource in the network.
Answer: D
QUESTION 58
Which command can you enter to cause the locally-originated Multicast Source Discovery Protocol Source-Active to be prevented from going to specific peers?
A. ip msdp mesh-group mesh-name {<peer-address>|<peer-name>}
B. ip msdp redistribute [list <acl>][asn as-access-list][route-map <map>]
C. ip msdp sa-filter out <peer> [list<acl>] [route-map<map>]
D. ip msdp default-peer {<peer-address> | <peer-name>}[prefix-list<list>]
E. ip msdp sa-filter in <peer> [list<acl>][route-map <map>]
Answer: C
QUESTION 59
CCMP (CCM mode Protocol) is based on which algorithm?
A. 3DES
B. Blowfish
C. RC5
D. AES
E. IDEA
Answer: D
QUESTION 60
Drag and Drop Question
Drag and drop each step in the SCEP process on the left into the correct order of operations on the right.
Answer:
Lead2pass gives the latest, authoritative and complete 400-251 braindumps for 400-251 exam, because of that, all of our candidates pass 400-251 certification without any problem. The biggest feature is the regular update of 400-251 PDF and VCE, which keeps our candidates’ knowledge up to date and ensures their 400-251 exam success.
400-251 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbkNSWnpMam9TWWM
2017 Cisco 400-251 exam dumps (All 336 Q&As) from Lead2pass:
http://www.lead2pass.com/400-251.html [100% Exam Pass Guaranteed]