2017 February Cisco Official New Released 400-251 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
Pass 400-251 exam with the latest Lead2pass 400-251 dumps: Lead2pass 400-251 exam questions and answers in PDF are prepared by our experts. Moreover, they are based on the recommended syllabus that covering all the 400-251 exam objectives.
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-251.html
QUESTION 141
Which two statements about the ISO are true? (Choose two)
A. The ISO is a government-based organization.
B. The ISO has three membership categories: member, correspondent, and subscribers.
C. Only member bodies have voting rights.
D. Correspondent bodies are small countries with their own standards organization.
E. Subscriber members are individual organizations.
Answer: BC
QUESTION 142
What feature on Cisco IOS router enables user identification and authorization based on per-user policies
A. CBAC
B. IPsec
C. Authentication proxy
D. NetFlow v9
E. Zone-based firewall
F. EEM
Answer: C
QUESTION 143
Which two statements about WPA 2 with AES CCMP encryption are true? (Choose two)
A. AES CCMP is a block cipher
B. It is compatible with TACACS+ servers running LEAP authentication
C. Every wireless packet sent to the host is tagged with CCMP frames
D. It uses a 256-bit hashing key
E. The MIC prevents modifications of wireless frames and replay attacks
F. It uses a 128-bit hashing key
Answer: AF
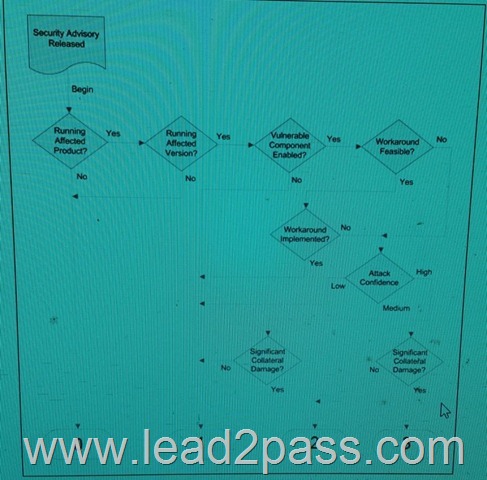
QUESTION 144
Refer to the exhibit. You have received an advisory that your organization could be running a vulnerable product. Using the Cisco Systems Rapid Risk Vulnerability Model, you determine that * Your organization is running an affected product on a vulnerable version of code vulnerable component is enabled and there is no feasible workaround *
There is medium confidence of an attack without significant collateral damage to the organization. According to the model what is the appropriate urgency for remediation?
A. priority maintenance process
B. contact ISP to trace attack
C. no action required
D. remove vulnerable device from service
E. standard maintenance process
F. immediate mitigation process
Answer: E
QUESTION 145
When configuration Cisco IOS firewall CBAC operation on Cisco routers, the “inspection rule” can be applied at which two location?(Choose two)
A. at the trusted and untrusted interfaces in the inbound direction.
B. at the trusted interface in the inbound direction.
C. at the trusted and untrusted interfaces in the outbound direction.
D. at the untrusted interface in the inbound direction.
E. at the trusted interface in the outbound direction.
F. at the trusted interface in the outbound direction.
Answer: BF
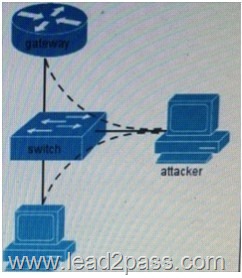
QUESTION 146
Refer to the exhibit, what type of attack is illustrated?
A. ICMP flood
B. ARP spoofing
C. IP address spoofing
D. CAM overflow
Answer: B
QUESTION 147
Which protocol does VNC use for remote access to a GUI?
A. RTPS
B. RARP
C. E6
D. SSH
E. RFB
Answer: D
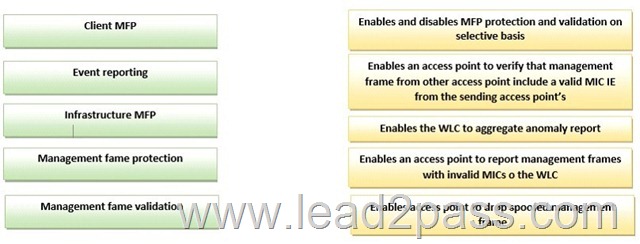
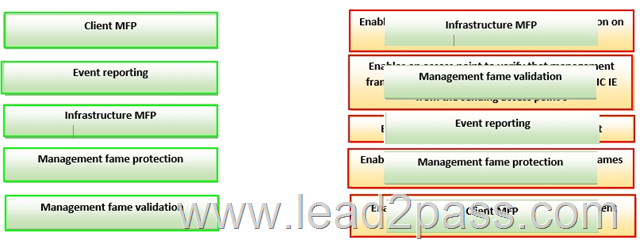
QUESTION 148
Drag and Drop Question
Drag each management frame protection feature on the left to the function it performs on the right.
Answer:
QUESTION 149
Which two statements about VPLS and VPWS are true? (Choose two)
A. VPLS Layer 2 VPNs support both full-mesh and hub-and-spoke implementations
B. VPWS only sends the data payload over an MPLS core
C. VPLS is intended for applications that require point-to-point access
D. VPWS supports multicast using a hub-and-spoke architecture
E. VPLS is intended for applications that require multipoint or broadcast access
F. VPWS supports point-to-point integration of Layer 2 and Layer 3 services over an MPLS cloud
Answer: EF
QUESTION 150
Refer to the exhibit, which conclusion can be drawn from this output? 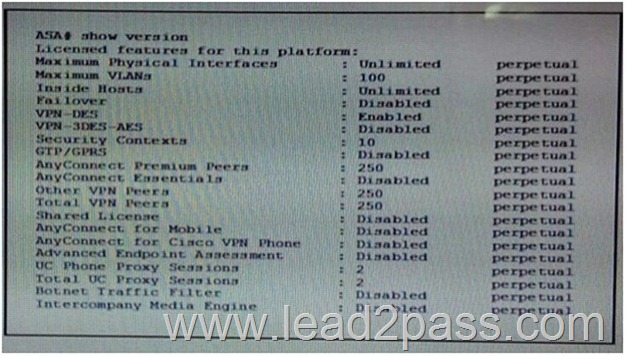
A. The license of the device supports multiple virtual firewalls
B. The license of the device allows the establishment of the maximum number of client- based, full- tunnel SSL VPNS for the platform
C. The license of the device allows for it to be used in a failover set
D. The license of the device allows a full-tunnel IPsec VPN using the Rijndael cipher
Answer: A
QUESTION 151
Which two statements about the SHA-1 algorithm are true? (Choose two)
A. The SHA-1 algorithm is considered secure because it always produces a unique hash for the same message.
B. The SHA-1 algorithm takes input message of any length and produces 160-bit hash output.
C. The SHA-1 algorithm is considered secure because it is possible to find a message from its hash.
D. The purpose of the SHA-1 algorithm is to provide data confidentiality.
E. The purpose of the SHA-1 algorithm is to provide data authenticity.
Answer: BE
QUESTION 152
Refer to the exhibit. What is the meaning of the given error massage?
A. Ike is disable on the remote peer
B. The mirrored crypto ACLs are mismatched
C. The pre-shared keys are mismatched
D. The PFS group are mismatched
Answer: C
QUESTION 153
Event Store is a component of which IPS application?
A. SensorApp
B. InterfaceApp
C. MainApp
D. NotificationApp
E. AuthenticationApp
Answer: C
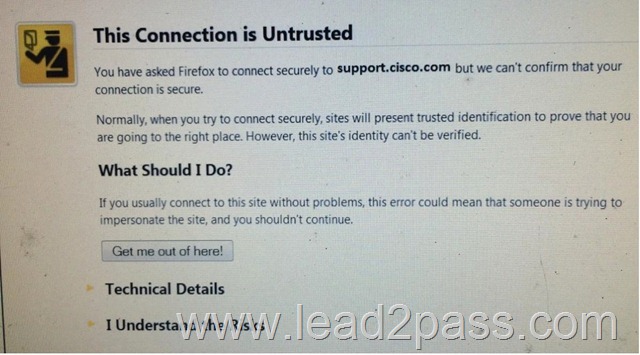
QUESTION 154
Refer to the exhibit. What are two TLS inspection methods you could implement for outbond internet traffic that can prevent the given untrusted error? (Choose two)
A. Add the self-signed CA certificate from the inspection appliance to the Trusted Root Certification Authority on the client
B. Apply an intermediate CA certificate from a trusted authority on the inspection appliance.
C. Download a copy of the private key from the content provider,
D. Update your organizational procedures to instruct users to click “I Understand the Risks” to accept the error and continue
E. Conditionally decrypt traffic based c$ trust level Store private keys in a FIPS Level 2 HSM on the inspection appliance
Answer: AB
QUESTION 155
Drag and Drop Question
Drag each IPv6 extension header on the left into the recommended order for more than one extension header in the same IPv6 packet on the right.
Answer:
QUESTION 156
What are two action you can take to protect against DDOS attacks on cisco router and switches?(Choose two)
A. Rate limit SYN packets
B. Filter the RFC-1918 address space
C. configuration IP snooping
D. implement MAC address filtering
E. Configuration PIM-SM
Answer: AB
QUESTION 157
Which two statements about SOX are true? (Choose two.)
A. SOX is an IEFT compliance procedure for computer systems security.
B. SOX is a US law.
C. SOX is an IEEE compliance procedure for IT management to produce audit reports.
D. SOX is a private organization that provides best practices for financial institution computer systems.
E. Section 404 of SOX is related to IT compliance.
Answer: BE
QUESTION 158
Which two options are disadvantages of MPLS layers 3 VPN services? (Choose two)
A. They requires cooperation with the service provider to implement transport of non-IP traffic.
B. SLAs are not supported by the service provider.
C. It requires customers to implement QoS to manage congestion in the network.
D. Integration between Layers 2 and 3 peering services is not supported.
E. They may be limited by the technology offered by the service provider.
F. They can transport only IPv6 routing traffic.
Answer: DE
QUESTION 159
Which RFC outlines BCP 84?
A. RFC 3704
B. RFC 2827
C. RFC 3030
D. RFC 2267
E. RFC 1918
Answer: A
QUESTION 160
Which option is a benefit of implementing RFC 2827?
A. prevents DoS from legitimate, non-hostile end systems
B. prevents disruption of special services such as Mobile IP
C. defeats DoS attacks which employ IP source address spoofing
D. restricts directed broadcasts at the ingress router
E. allows DHCP or BOOTP packets to reach the relay agents as appropriate
Answer: C
Comparing with others’, you will find our 400-251 exam questions are more helpful and precise since all the 400-251 exam content is regularly updated and has been checked for accuracy by our team of Cisco expert professionals.
400-251 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbkNSWnpMam9TWWM
2017 Cisco 400-251 exam dumps (All 336 Q&As) from Lead2pass:
http://www.lead2pass.com/400-251.html [100% Exam Pass Guaranteed]