2016 October Cisco Official New Released 300-209 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
Good news, Lead2pass has updated the 300-209 exam dumps. With all the questions and answers in your hands, you will pass the Cisco 300-209 exam easily.
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/300-209.html
QUESTION 41
Which NGE IKE Diffie-Hellman group identifier has the strongest cryptographic properties?
A. group 10
B. group 24
C. group 5
D. group 20
Answer: D
QUESTION 42
What is the Cisco recommended TCP maximum segment on a DMVPN tunnel interface when the MTU is set to 1400 bytes?
A. 1160 bytes
B. 1260 bytes
C. 1360 bytes
D. 1240 bytes
Answer: C
QUESTION 43
Which technology does a multipoint GRE interface require to resolve endpoints?
A. ESP
B. dynamic routing
C. NHRP
D. CEF
E. IPSec
Answer: C
QUESTION 44
Which two cryptographic technologies are recommended for use with FlexVPN? (Choose two.)
A. SHA (HMAC variant)
B. Diffie-Hellman
C. DES
D. MD5 (HMAC variant)
Answer: AB
QUESTION 45
Which command configures IKEv2 symmetric identity authentication?
A. match identity remote address 0.0.0.0
B. authentication local pre-share
C. authentication pre-share
D. authentication remote rsa-sig
Answer: D
QUESTION 46
Which two examples of transform sets are contained in the IKEv2 default proposal? (Choose two.)
A. aes-cbc-192, sha256, 14
B. 3des, md5, 5
C. 3des, sha1, 1
D. aes-cbc-128, sha, 5
Answer: BD
QUESTION 47
What is the default storage location of user-level bookmarks in an IOS clientless SSL VPN?
A. disk0:/webvpn/{context name}/
B. disk1:/webvpn/{context name}/
C. flash:/webvpn/{context name}/
D. nvram:/webvpn/{context name}/
Answer: C
QUESTION 48
Which command will prevent a group policy from inheriting a filter ACL in a clientless SSL VPN?
A. vpn-filter none
B. no vpn-filter
C. filter value none
D. filter value ACLname
Answer: C
QUESTION 49
Which command specifies the path to the Host Scan package in an ASA AnyConnect VPN?
A. csd hostscan path image
B. csd hostscan image path
C. csd hostscan path
D. hostscan image path
Answer: B
QUESTION 50
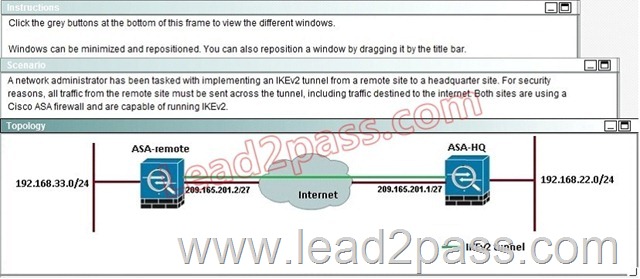
Hotspot Questions
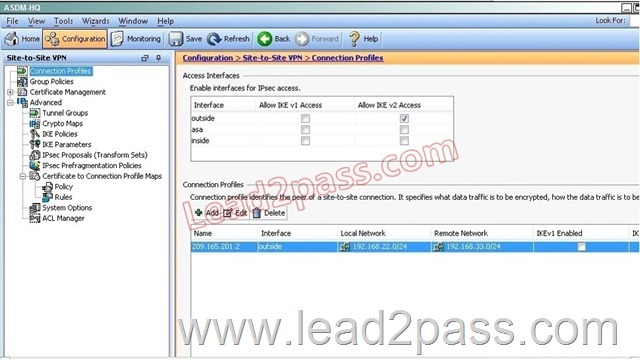
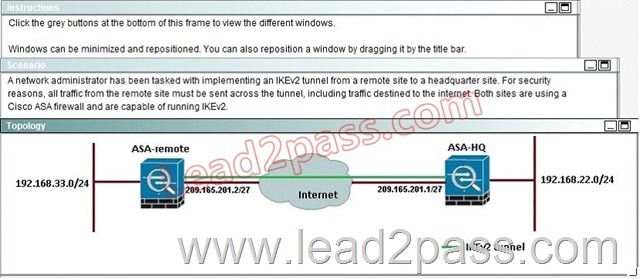
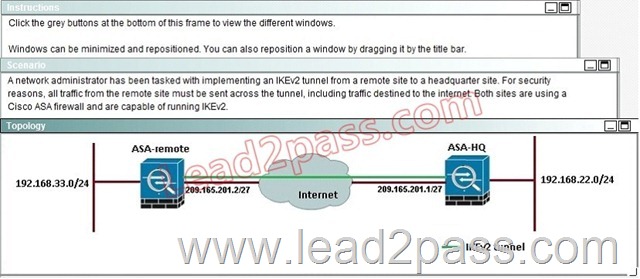
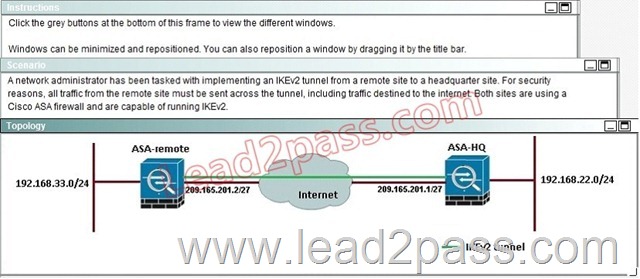
When a tunnel is initiated by the headquarter ASA, which one of the following Diffie- Hellman groups is selected by the headquarter ASA during CREATE_CHILD_SA exchange?
A. 1
B. 2
C. 5
D. 14
E. 19
Answer: C
Explanation:
Traffic initiated by the HQ ASA is assigned to the static outside crypto map, which shown below to use DH group 5.
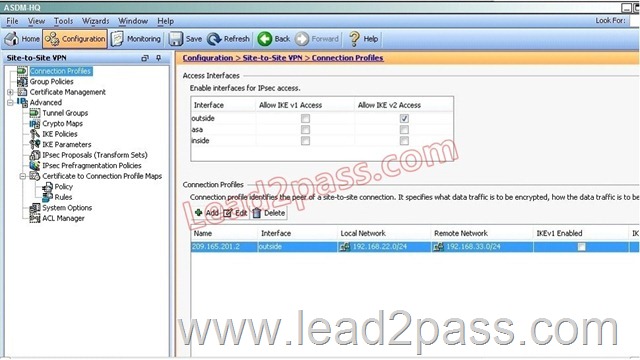
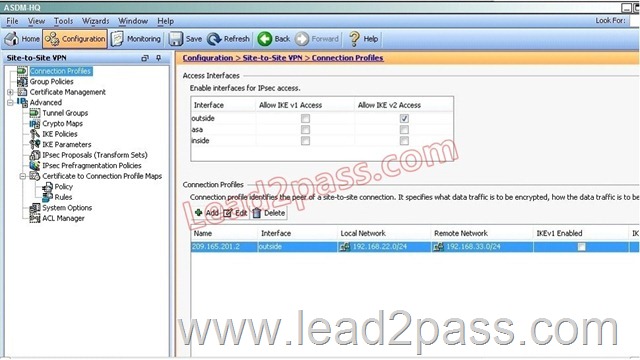
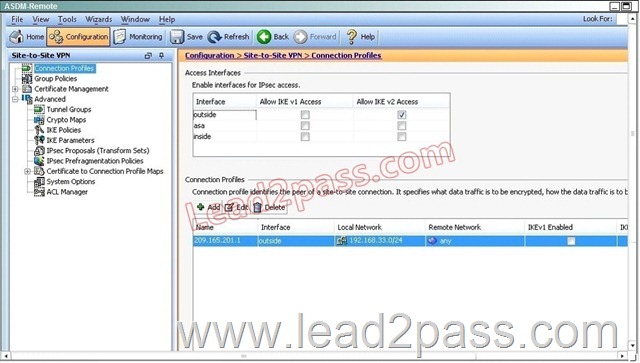
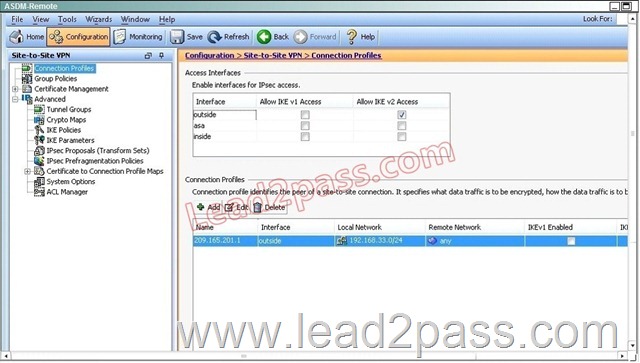
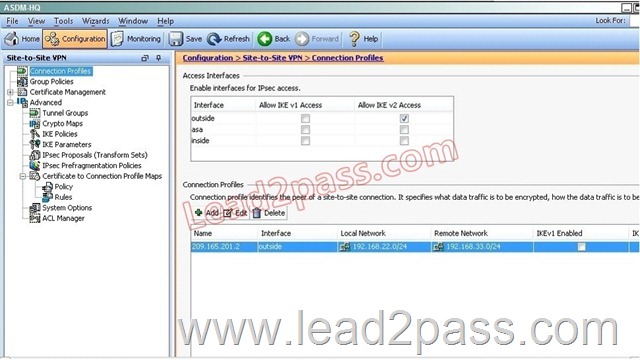
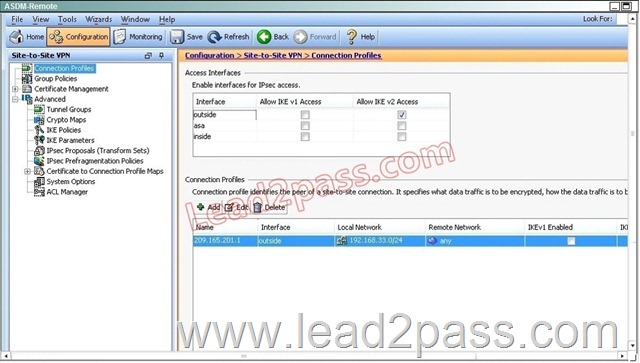
Based on the provided ASDM configuration for the remote ASA, which one of the following is correct?
A. An access-list must be configured on the outside interfaceto permit inbound VPN traffic
B. A route to 192.168.22.0/24 will not be automatically installed in the routing table
C. The ASA will use a window of 128 packets (64×2) to perform the anti-replay check _
D. The tunnel can also be established on TCP port 10000
Answer: C
Explanation:
Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence number to each encrypted packet. The decryptor keeps track of which packets it has seen on the basis of these numbers. Currently, the default window size is 64 packets. Generally, this number (window size) is sufficient, but there are times when you may want to expand this window size. The IPsec Anti-Replay Window: Expanding and Disabling feature allows you to expand the window size, allowing the decryptor to keep track of more than 64 packets.
QUESTION 52
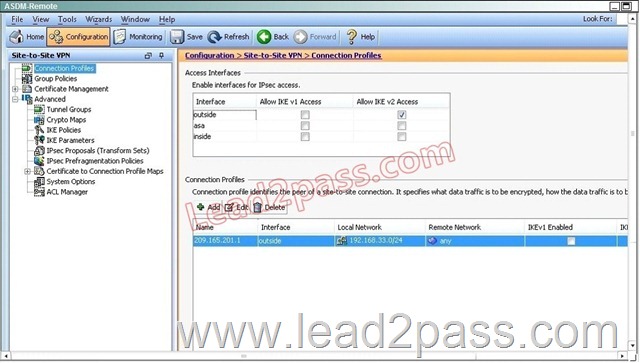
Hotspot Questions
If the IKEv2 tunnel were to establish successfully, which encryption algorithm would be used to encrypt traffic?
A. DES
B. 3DES
C. AES
D. AES192
E. AES256
Answer: E
Explanation:
Both ASA’s are configured to support AES 256, so during the IPSec negotiation they will use the strongest algorithm that is supported by each peer.
QUESTION 53
Hotspot Questions
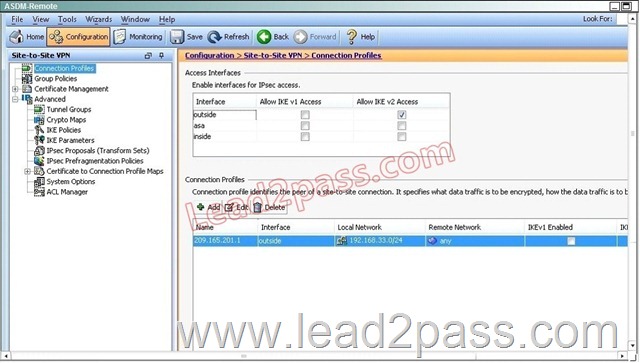
After implementing the IKEv2 tunnel, it was observed that remote users on the 192.168.33.0/24 network are unable to access the internet. Which of the following can be done to resolve this problem?
A. Change the Diffie-Hellman group on the headquarter ASA to group5forthe dynamic crypto map
B. Change the remote traffic selector on the remote ASA to 192.168.22.0/24
C. Change to an IKEvI configuration since IKEv2 does not support a full tunnel with static peers
D. Change the local traffic selector on the headquarter ASA to 0.0.0.0/0
E. Change the remote traffic selector on the headquarter ASA to 0.0.0.0/0
Answer: B
Explanation:
The traffic selector is used to determine which traffic should be protected (encrypted over the IPSec tunnel). We want this to be specific, otherwise Internet traffic will also be sent over the tunnel and most likely dropped on the remote side. Here, we just want to protect traffic from 192.168.33.0/24 to 192.168.22.0/24.
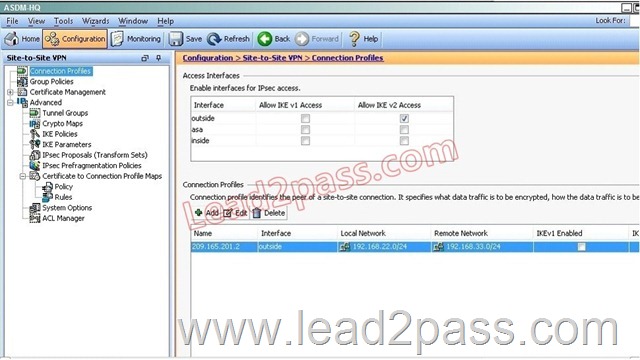
QUESTION 54
Hotspot Questions
Which option shows the correct traffic selectors for the child SA on the remote ASA, when the headquarter ASA initiates the tunnel?
A. Local selector 192.168.33.0/0-192.168.33.255/65535
Remote selector 192.168.20.0/0-192.168.20.255/65535
B. Local selector 192.168.33.0/0-192.168.33.255/65535
Remote selector 192.168.22.0/0-192.168.22.255/65535
C. Local selector 192.168.22.0/0-192.168.22.255/65535
Remote selector 192.168.33.0/0-192.168.33.255/65535
D. Local selector 192.168.33.0/0-192.168.33.255/65535
Remote selector 0.0.0.0/0 – 0.0.0.0/65535
E. Local selector 0.0.0.0/0 – 0.0.0.0/65535
Remote selector 192.168.22.0/0 -192.168.22.255/65535
Answer: B
Explanation:
The traffic selector is used to determine which traffic should be protected (encrypted over the IPSec tunnel). We want this to be specific, otherwise Internet traffic will also be sent over the tunnel and most likely dropped on the remote side. Here, we just want to protect traffic from 192.168.33.0/24 (THE LOCAL SIDE) to 192.168.22.0/24 (THE REMOTE SIDE).
QUESTION 55
Lab Simulation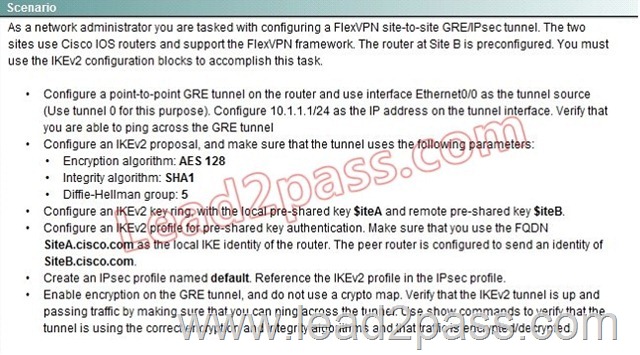
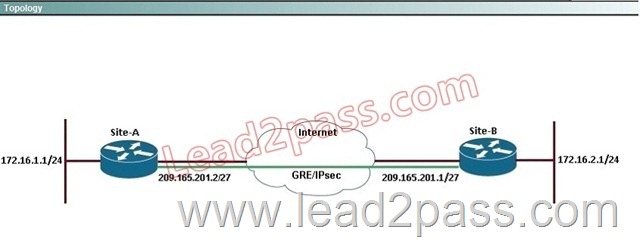
Answer:
Step 1: configure key ring
crypto ikev2 keyring mykeys
peer SiteB.cisco.com
address 209.161.201.1
pre-shared-key local SiteA
pre-shared key remote SiteB
Step 2: Configure IKEv2 profile
Crypto ikev2 profile default
identity local fqdn SiteA.cisco.com
Match identity remote fqdn SiteB.cisco.com
Authentication local pre-share
Authentication remote pre-share
Keyring local mykeys
Step 3: Create the GRE Tunnel and apply profile
crypto ipsec profile default
set ikev2-profile default
Interface tunnel 1
ip address 10.1.1.1
Tunnel source eth 0/0
Tunnel destination 209.165.201.1
tunnel protection ipsec profile default
end
QUESTION 56
Which two are characteristics of GETVPN? (Choose two.)
A. The IP header of the encrypted packet is preserved
B. A key server is elected among all configured Group Members
C. Unique encryption keys are computed for each Group Member
D. The same key encryption and traffic encryption keys are distributed to all Group Members
Answer: AD
QUESTION 57
A company has decided to migrate an existing IKEv1 VPN tunnel to IKEv2. Which two arevalid configuration constructs on a Cisco IOS router? (Choose two.)
A. crypto ikev2 keyring keyring-name
peer peer1
address 209.165.201.1 255.255.255.255
pre-shared-key local key1
pre-shared-key remote key2
B. crypto ikev2 transform-set transform-set-name esp-3des esp-md5-hmac
esp-aes esp-sha-hmac
C. crypto ikev2 map crypto-map-name
set crypto ikev2 tunnel-group tunnel-group-name
set crypto ikev2 transform-set transform-set-name
D. crypto ikev2 tunnel-group tunnel-group-name
match identity remote address 209.165.201.1
authentication local pre-share
authentication remote pre-share
E. crypto ikev2 profile profile-name
match identity remote address 209.165.201.1
authentication local pre-share
authentication remote pre-share
Answer: AE
QUESTION 58
Which four activities does the Key Server perform in a GETVPN deployment? (Choose four.)
A. authenticates group members
B. manages security policy
C. creates group keys
D. distributes policy/keys
E. encrypts endpoint traffic
F. receives policy/keys
G. defines group members
Answer: ABCD
QUESTION 59
Where is split-tunneling defined for remote access clients on an ASA?
A. Group-policy
B. Tunnel-group
C. Crypto-map
D. Web-VPN Portal
E. ISAKMP client
Answer: A
QUESTION 60
Which of the following could be used to configure remote access VPN Host-scan and pre- login policies?
A. ASDM
B. Connection-profile CLI command
C. Host-scan CLI command under the VPN group policy
D. Pre-login-check CLI command
Answer: A
Once there are some changes on 300-209 exam questions, we will update the study materials timely to make sure that our customer can download the latest edition.
300-209 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDODI1TDlUT1lBV00
2016 Cisco 300-209 exam dumps (All 237 Q&As) from Lead2pass:
http://www.lead2pass.com/300-209.html [100% Exam Pass Guaranteed]